The WebRAT malware is now being distributed via GitHub repositories that declare to host proof-of-concept exploits for not too long ago disclosed vulnerabilities.
Beforehand unfold via pirated software program and cheats for video games like Roblox, Counter Strike, and Rust, WebRAT is a backdoor with info-stealing capabilities that emerged in the beginning of the yr.
In accordance with a report from Photo voltaic 4RAYS in Might, WebRAT can steal credentials for Steam, Discord, and Telegram accounts, in addition to cryptocurrency pockets information. It could additionally spy on victims via webcams and seize screenshots.
Since not less than September, the operators began to ship the malware via fastidiously crafted repositories claiming to offer an exploit for a number of vulnerabilities that had been coated in media stories. Amongst them had been:
- CVE-2025-59295 – A heap-based buffer overflow within the Home windows MSHTML/Web Explorer element, enabling arbitrary code execution by way of specifically crafted information despatched over the community.
- CVE-2025-10294 – A crucial authentication bypass within the OwnID Passwordless Login plugin for WordPress. As a consequence of improper validation of a shared secret, unauthenticated attackers may log in as arbitrary customers, together with directors, with out credentials.
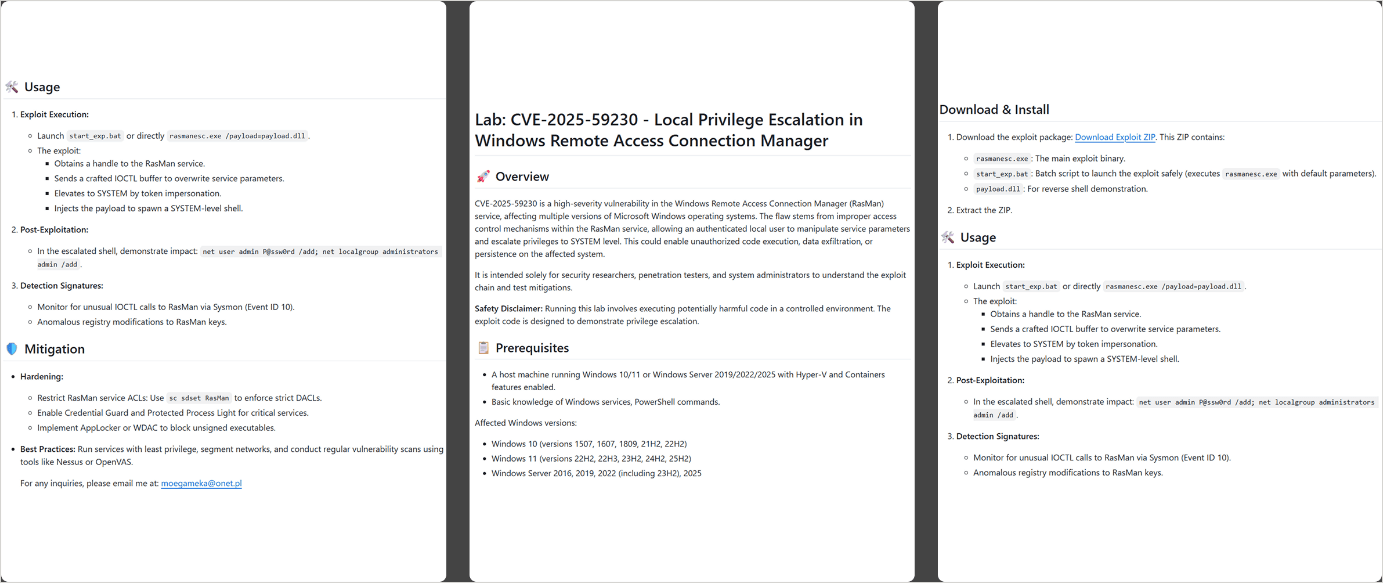
- CVE-2025-59230 – An elevation-of-privilege (EoP) vulnerability in Home windows’ Distant Entry Connection Supervisor (RasMan) service. A regionally authenticated attacker may exploit improper entry management to escalate their privileges to SYSTEM stage on affected Home windows installations.
Safety researchers at Kaspersky found 15 repositories distributing WebRAT, all of them offering details about the difficulty, what the alleged exploit does, and the out there mitigations.
As a result of approach the data is structured, Kaspersky believes that the textual content was generated utilizing a synthetic intelligence mannequin.
Supply: Kaspersky
The malware has a number of strategies to determine persistence, together with Home windows Registry modifications, the Job Scheduler, and injecting itself into random system directories.
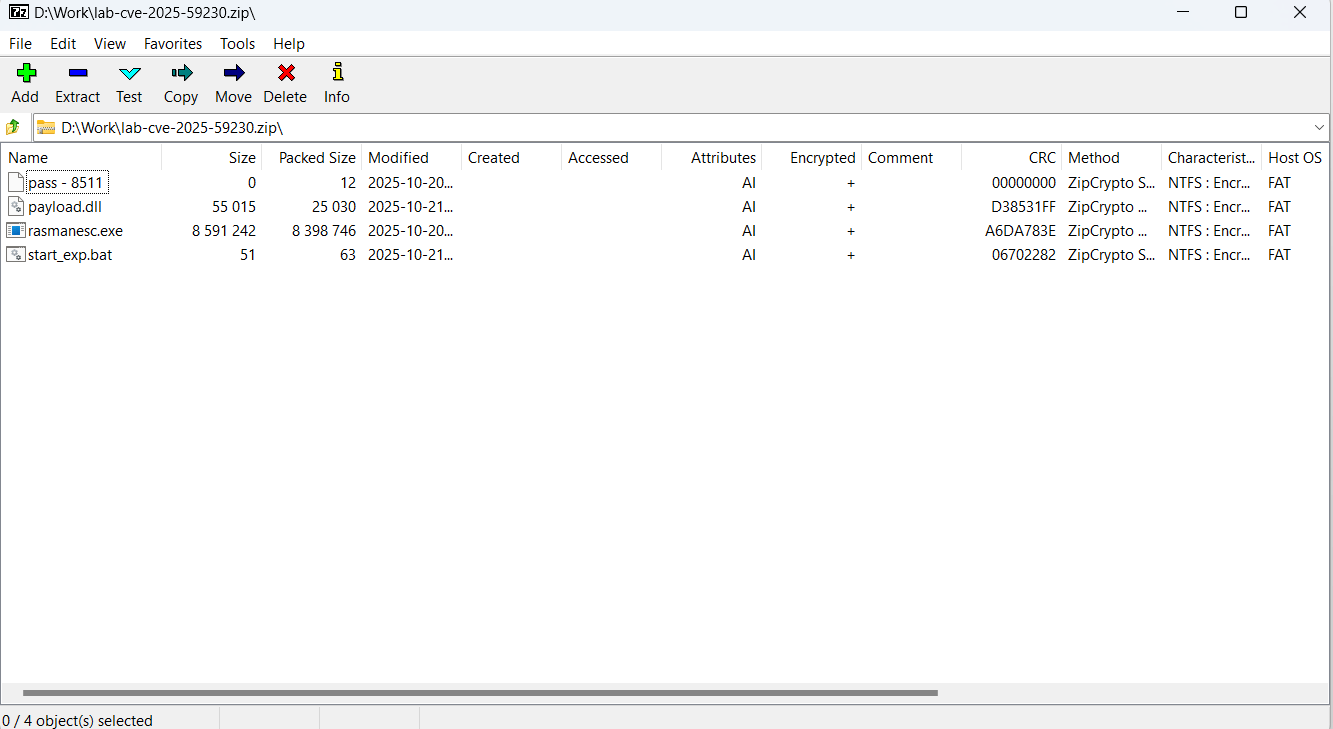
Kaspersky researchers say that the pretend exploits are delivered within the type of a password-protected ZIP file containing an empty file with the password as its identify, a corrupted decoy DLL file appearing as a decoy, a batch file used within the execution chain, and the primary dropper named rasmanesc.exe.
Supply: Kaspersky
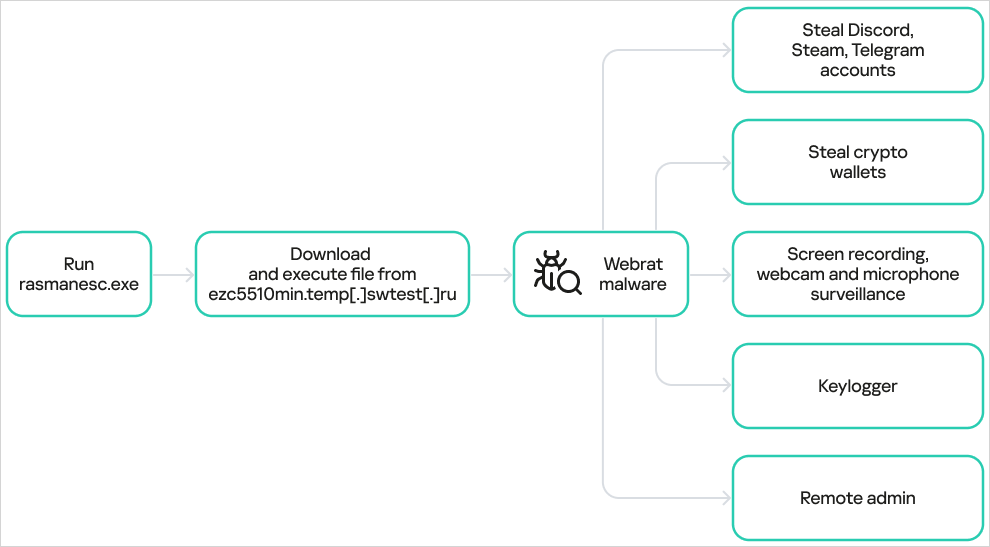
In accordance with the analysts, the dropper elevates privileges, disables Home windows Defender, after which downloads and executes WebRAT from a hardcoded URL.
Kaspersky notes that the WebRAT variant used on this marketing campaign is not any completely different from beforehand documented samples and lists the identical capabilities described in previous stories.
Supply: Kaspersky
Utilizing pretend exploits on GitHub to lure unsuspecting customers into putting in malware just isn’t a brand new tactic, because it has been extensively documented up to now [1, 2, 3, 4]. Extra not too long ago, risk actors promoted a pretend “LDAPNightmare” exploit on GitHub to unfold infostealing malware.
All malicious GitHub repositories associated to the WebRAT marketing campaign that Kaspersky uncovered have been eliminated. Nonetheless, builders and infosec lovers needs to be cautious in regards to the sources they use, as risk actors can submit new lures below completely different writer names.
The overall rule when testing exploits or code that comes from a doubtlessly untrusted supply is to run them in a managed, remoted surroundings.
Damaged IAM is not simply an IT drawback – the impression ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM seems like, and a easy guidelines for constructing a scalable technique.



