The weakest hyperlink within the privateness of cryptocurrency transactions is usually outdoors the blockchain. There are applied sciences akin to stealth addresses and subaddresses to attempt to thwart makes an attempt to hyperlink transactions to people. They do a great job of anonymizing transaction information, however the weak hyperlink could also be metadata, as is usually the case.
Cryptocurrency nodes flow into transaction information utilizing a peer-to-peer community. An entity working a number of nodes can evaluate when information arrived at every of its nodes and triangulate to deduce which node first despatched a set of transactions. The Dandelion protocol, and its refinement Dandelion++, goals to mitigate this threat. Dandelion++ is presently utilized in Monero and some different cash; different cryptocurrencies have thought of or are contemplating utilizing it.
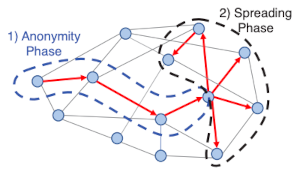
The thought behind the Dandelion protocol is to have a “stalk” interval and a “diffusion” interval. Think about information working up the stalk of a dandelion plant earlier than diffusing like seeds within the wind. The same old P2P course of is analogous to easily blowing on the seed head [1].
Throughout the stalk interval, info travels from one node to 1 node. Then after some variety of hops, the diffusion course of begins; the ultimate node within the stalk interval diffuses the data to all its friends. An observer with substantial however not full visibility of the community could possibly decide which node initiated the diffusion, however possibly not the node on the different finish of the stem.
A pure query is how this differs from one thing like Tor. In a nutshell, Tor gives id safety earlier than you enter a P2P community, and Dandelion gives id safety inside the P2P community.
For extra particulars, see the unique paper on Dandelion [2].
Associated posts
[1] The unique paper on Dandelion makes use of a dandelion seed because the metaphor for the protocol. “The title ‘dandelion spreading’ displays the spreading sample’s resemblance to a dandelion seed head and refers back to the diagram under. Nonetheless, different sources seek advice from the stalk and head of the dandelion plant, not only a single seed. Each psychological photographs work because the plant has a barely fractal construction with a single seed trying one thing just like the plant.
[2] Shaileshh Bojja Venkatakrishnan, Giulia Fanti, Pramod Viswanath. Dandelion: Redesigning the Bitcoin Community for Anonymity. Proceedings of the ACM on Measurement and Evaluation of Computing Methods, Quantity 1, Challenge 1 Article No.: 22, Pages 1–34. Accessible right here: https://doi.org/10.1145/3084459.

