As organizations plan their defenses for the instant future, 51% of companies rank cybersecurity assaults and breaches as the highest threat to their efficiency in 2026.
On the similar time, the ratio of cybersecurity spending to monetary losses is staggering; whereas world spending was $185 billion in 2024 towards $9.22 trillion in losses, this hole is projected to extend to 68 occasions by 2030, with $262 billion in spending versus $18 trillion in losses.
This stark monetary actuality exhibits that conventional protection mechanisms are not enough. On this weblog, we are going to concentrate on AI for Cybersecurity, defensive methods, threat administration, and workforce adaptation that should structurally change to handle the evolution of automated and clever threats.
Summarize this text with ChatGPT
Get key takeaways & ask questions
The Rising Dynamics of AI-Pushed Threats
The standard mannequin of cybersecurity relied on figuring out recognized patterns of malicious code, however the introduction of machine studying has allowed attackers to maneuver past these predictable strategies.
Trendy threats at the moment are characterised by their capacity to be taught from the environments they infect, making them more durable to trace and neutralize utilizing customary software program.
Attackers are utilizing synthetic intelligence in cybersecurity not simply to maneuver quicker, however to create extremely customized campaigns that exploit human psychology and system vulnerabilities concurrently.
The evolution of those techniques is outlined by a number of crucial developments in how malicious actors make the most of automated intelligence:
- Autonomous and Self-Evolving Malware: Malicious software program not requires fixed directions from a central server to execute its mission. As an alternative, it will possibly enter a community and independently analyze the atmosphere to search out essentially the most priceless knowledge or the weakest safety factors, usually altering its personal code to keep away from being detected by antivirus scanners.
- Hyper-Personalised Social Engineering: By processing huge quantities of public knowledge, attackers can generate phishing emails or messages that completely mimic the tone and magnificence of a trusted colleague or government. This removes the widespread warning indicators of fraud, resembling poor grammar or generic greetings, making these assaults extremely profitable.
- Adversarial Manipulation of Protection Programs: As a result of many safety instruments now use synthetic intelligence to detect threats, attackers have begun concentrating on the logic of those instruments. By introducing “poisoned” knowledge right into a system’s studying course of, they will trick the safety software program into ignoring particular kinds of malicious exercise.
- Giant-Scale Vulnerability Discovery: Automated instruments can scan thousands and thousands of traces of code in seconds to search out “zero-day” vulnerabilities that haven’t but been found by software program builders. This enables attackers to use weaknesses in widespread functions earlier than a patch could be created or deployed.
These developments imply that the window of time obtainable to answer an assault has shrunk from days to seconds.
When threats can suppose and adapt on their very own, a handbook response from a human safety staff is commonly too gradual to forestall knowledge theft or system lockdowns.
Organizations should subsequently acknowledge that they’re not simply preventing human hackers, however extremely environment friendly, automated software program brokers.
Strengthening the Core Safety Buildings for Higher Safety
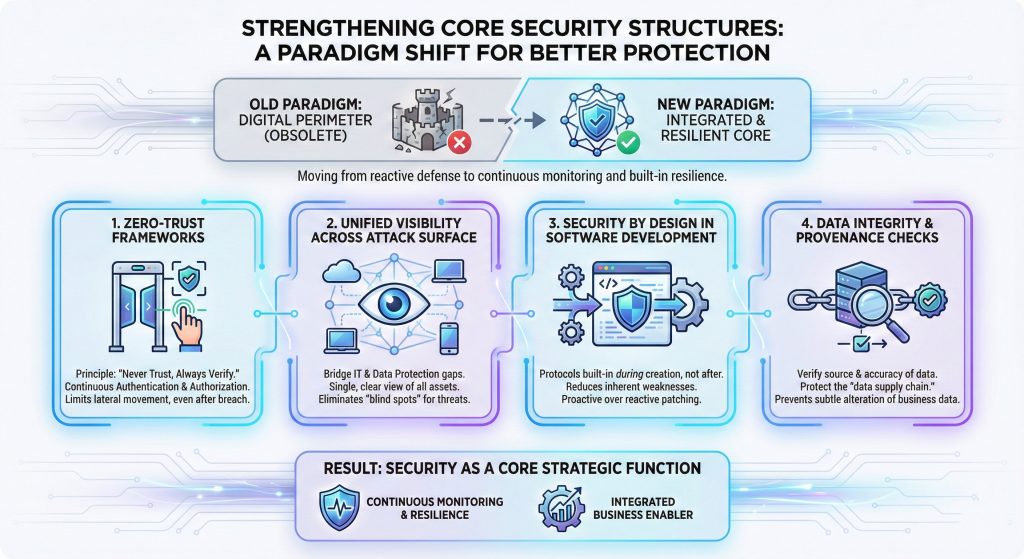
Defending a corporation on this atmosphere requires extra than simply shopping for new software program; it requires an entire change in how a community is constructed and managed.
The previous concept of a “digital perimeter” the place everybody inside a constructing is trusted, and everybody outdoors is blocked, is not related in a world of distant work and cloud computing.
Safety should now be built-in into each single gadget, software, and person interplay throughout the enterprise ecosystem.
To handle these vulnerabilities, organizations are transferring towards a extra built-in and disciplined structural mannequin:
- Implementation of Zero-Belief Frameworks: This technique operates on the precept of “by no means belief, at all times confirm.” Each person and gadget should be repeatedly authenticated and licensed to entry particular knowledge, making certain that even when an attacker positive factors entry, they can not transfer freely throughout the whole community.
- Unified Visibility Throughout the Assault Floor: Safety groups should bridge the hole between IT operations and knowledge safety to achieve a single, clear view of all linked property. This consists of figuring out each laptop computer, cloud server, and cell gadget to make sure that no “blind spots” exist the place an automatic risk might disguise.
- Safety by Design in Software program Growth: Quite than checking for safety flaws after a product is completed, safety protocols at the moment are constructed into the very starting of the software program creation course of. This reduces the variety of inherent weaknesses that may be exploited later by clever scanning instruments.
- Knowledge Integrity and Provenance Checks: Organizations should implement strict controls to confirm the supply and accuracy of the information they use to coach their very own inside programs. Defending the “knowledge provide chain” ensures that the knowledge used for enterprise choices has not been subtly altered by an outdoor social gathering.
By adopting these structural adjustments, companies transfer from reactive protection to steady monitoring and built-in resilience, making safety a core strategic perform reasonably than a separate division.
This shift can be creating sturdy expertise demand, with authorities projections estimating almost 140,100 job openings yearly for software program and safety testing professionals via 2033, highlighting how crucial superior safety experience has grow to be to sustained digital development.
For these trying to confidently lead on this evolving digital atmosphere, the Certificates Program in Generative AI & Brokers Fundamentals from Johns Hopkins College supplies a extremely related, 8-week on-line studying path.
This program requires no programming expertise and equips technical leaders and enterprise professionals with a dependable basis in AI, together with essential modules on accountable AI practices and safety.
How does this program empower your profession?
This government training program is particularly designed to assist professionals leverage synthetic intelligence in cybersecurity whereas understanding the crucial guardrails required for safe enterprise deployment. Right here is the way it immediately advantages you:
- Sort out AI Safety Dangers Head-On: The curriculum dedicates particular focus to Accountable AI, educating you the best way to determine main Giant Language Mannequin (LLM) safety dangers resembling immediate injection, knowledge poisoning, and jailbreaking.
- Apply Safety Frameworks to AI: You’ll learn to actively apply the CIA Triad (Confidentiality, Integrity, Availability) to evaluate and mitigate safety dangers inside LLM deployments.
- Perceive Provide Chain Vulnerabilities: Aligning completely with the necessity for knowledge provenance, this system explains how provide chain vulnerabilities and repair denial can compromise AI reliability and accountability.
- Construct Sensible AI Abilities With out Coding: You’ll be taught to design agentic workflows, perceive Immediate Engineering, and apply AI brokers to enterprise operations, all without having any prior programming data.
In an period the place cybersecurity and AI have gotten deeply interconnected, applications like this allow professionals to not solely perceive rising applied sciences but additionally deploy them responsibly and securely.
As assaults grow to be smarter, defensive instruments should additionally achieve the flexibility to cause and act with out ready for human intervention.
The objective of a contemporary protection system is to realize “predictive safety,” the place the software program can anticipate an attacker’s subsequent transfer primarily based on delicate adjustments in community habits.
This requires a transition from reactive instruments that fireside alerts after an incident to proactive programs that actively hunt for threats. The effectiveness of those proactive methods depends on a number of key technical capabilities:
- Behavioral Anomaly Detection: As an alternative of in search of a selected virus, these programs be taught what “regular” appears to be like like for each worker and server. If a quiet accountant all of the sudden begins downloading hundreds of encrypted recordsdata at midnight, the system acknowledges this as an anomaly and instantly restricts their entry.
- Automated Incident Triage and Response: Superior safety platforms can now deal with the primary phases of an assault mechanically. They’ll isolate contaminated computer systems, block suspicious internet site visitors, and reset compromised passwords in real-time, permitting human analysts to concentrate on investigating the basis trigger.
- Steady Menace Looking: Specialised software program brokers continuously crawl via a corporation’s inside logs and exterior risk databases to search out indicators of hidden intruders. This energetic looking out helps discover “low and gradual” assaults that attempt to keep underneath the radar for months.
- Clever Content material Filtering: Communication instruments now use context-aware evaluation to cease deepfake audio or video and phishing makes an attempt earlier than they attain an worker’s inbox, successfully neutralizing the attacker’s most potent software.
Utilizing these superior methodologies permits a safety staff to handle a a lot larger quantity of threats than was beforehand doable.
To successfully implement these superior, automated protection mechanisms, from behavioral anomaly detection to steady risk searching, safety professionals want specialised, up-to-date coaching.
Constructing the potential to transition a corporation from a reactive posture to a predictive safety mannequin requires hands-on expertise with fashionable instruments and defensive frameworks.
For these able to grasp these proactive methodologies and keep forward of automated threats, exploring industry-aligned Cyber Safety Programs supplies the important sensible expertise and strategic data required to confidently fortify any digital infrastructure.
The Function of Agentic Programs in Safety Operations
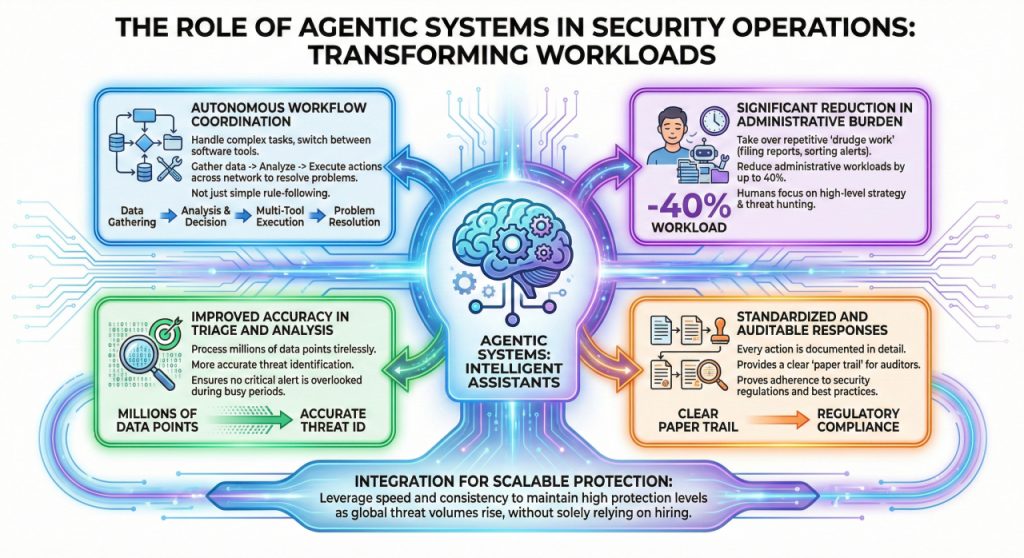

A big breakthrough in managing safety workloads is the usage of “agent” programs that may suppose via an issue and execute a number of steps to resolve it. These instruments are reworking the day-to-day operations of safety departments by appearing as clever assistants:
- Autonomous Workflow Coordination: In contrast to easy automation that follows one rule, agentic programs can deal with complicated duties that require switching between completely different software program instruments. They’ll collect knowledge, analyze it, after which execute a sequence of actions throughout the community to resolve an issue.
- Important Discount in Administrative Burden: By taking up the repetitive “drudge work” of safety, resembling submitting reviews and sorting via low-level alerts, these programs can scale back administrative workloads by as much as 40%. This enables human groups to spend their time on high-level technique and risk searching.
- Improved Accuracy in Triage and Evaluation: Automated brokers can course of thousands and thousands of information factors with out getting drained or distracted. This results in extra correct identification of threats and ensures that no crucial alert is ignored throughout a busy interval.
- Standardized and Auditable Responses: When an agent handles a safety activity, each motion they take is documented intimately. This supplies a transparent “paper path” for auditors and helps the group show it’s following all needed safety laws and finest practices.
The mixing of those programs permits safety departments to scale their efforts with out essentially hiring a whole bunch of recent employees members.
By leveraging the pace and consistency of agentic programs, organizations can keep a excessive stage of safety whilst the amount of world threats continues to rise.
Guaranteeing Compliance By Efficient Threat and Governance Practices
Managing threat in an AI for Cybersecurity requires new guidelines and clear accountability. Governance should bridge the hole between technical capabilities and moral obligations to make sure that safety instruments are used successfully and safely:
- Adherence to Standardized Threat Frameworks: Organizations ought to align their operations with globally acknowledged requirements, such because the NIST AI Threat Administration Framework. These pointers present a structured option to determine, measure, and handle the precise dangers related to utilizing clever programs in a company atmosphere.
- Institution of Moral Use Insurance policies: Firms should create clear guidelines for the way automated instruments are used, significantly concerning worker privateness and knowledge utilization. This prevents “shadow AI,” the place staff use unauthorized instruments which may by accident leak delicate firm data into public databases.
- Rigorous Third-Get together and Provide Chain Audits: As companies rely extra on outdoors distributors for software program and knowledge companies, they need to confirm that these companions keep excessive safety requirements. A vulnerability in a single provider can present a “backdoor” into dozens of different firms, making provide chain safety a prime precedence.
- Emphasis on Human-in-the-Loop Oversight: Whereas automation supplies pace, human judgment stays important for complicated decision-making and moral issues. Governance fashions should outline precisely when a human should intervene, particularly in high-stakes conditions like shutting down crucial enterprise programs throughout a suspected assault.
Sturdy governance ensures that, as a corporation adopts extra highly effective know-how, it does so with a full understanding of the potential penalties.
This creates a steadiness the place the advantages of automation are maximized whereas the authorized and operational dangers are saved underneath strict management.
Nonetheless, establishing these strong frameworks and sustaining a powerful organizational safety posture requires specialised technical experience.
With an IBM examine revealing that 95% of cybersecurity breaches end result from human error, cultivating a extremely skilled workforce is essentially the most crucial protection a corporation can deploy.
To satisfy the surging demand for expertise, professionals should systematically improve their talent set,s and that’s the place applications like The Put up Graduate Program in Cybersecurity, introduced by the McCombs Faculty of Enterprise at The College of Texas at Austin in collaboration with Nice Studying, are recognized to be a one-stop resolution.
Designed by main college, this curriculum provides you the instruments to research assaults, construct strong cybersecurity programs, and achieve a aggressive edge within the job market. Right here is how this system immediately interprets to profession development:
- Grasp Governance, Threat, and Compliance (GRC): You’ll achieve a deep understanding of significant requirements and frameworks to construct a powerful organizational safety posture. The curriculum develops your technical experience in navigating knowledge safety legal guidelines like GDPR and DPDP, making use of ISO 27001:2022, and managing third-party provide chain dangers.
- Perceive and Fight Trendy Cyber Assaults: You’ll be taught to view threats from an adversary’s lens, using frameworks like MITRE ATT&CK and the Cyber Kill Chain. This prepares you to acknowledge and defend towards threats resembling Superior Persistent Threats (APTs) and Ransomware.
- Design and Implement Safety Controls: You’ll uncover efficient strategies for making use of safety methods, diving deeply into Endpoint Detection and Response (EDR), Id and Entry Administration (IDAM), Knowledge Loss Prevention (DLP), and steady monitoring utilizing SIEM.
- Acquire Sensible, Arms-On Expertise: This system goes past principle by providing in depth lab classes. You’ll follow capturing community site visitors with Wireshark, configuring Subsequent Technology Firewalls (NGFW), executing internet software penetration assessments, and securing knowledge on Microsoft Azure.
By constructing experience throughout GRC, risk intelligence, safety structure, and hands-on protection practices, this program equips you to cut back organizational threat, strengthen resilience, and place your self as a trusted cybersecurity chief in an more and more high-stakes digital dangers.
Conclusion
Adapting cybersecurity pondering for the age of AI requires a transfer away from the “shield and react” mindset of the previous. It’s not sufficient to attend for an assault to occur after which attempt to repair it; as an alternative, safety should be an energetic, clever, and foundational a part of each enterprise course of.
This transformation includes deploying autonomous defenses that may match the pace of attackers, restructuring networks to take away unearned belief, and constructing a workforce that’s deeply expert within the nuances of recent know-how.
By specializing in resilience, governance, and steady adaptation, organizations can navigate this new period with confidence, making certain they keep forward of the curve in a quickly altering risk atmosphere.

