Attackers are utilizing the open-source red-team instrument RedTiger to construct an infostealer that collects Discord account information and cost info.
The malware can even steal credentials saved within the browser, cryptocurrency pockets information, and recreation accounts.
RedTiger is a Python-based penetration testing suite for Home windows and Linux that bundles choices for scanning networks and cracking passwords, OSINT-related utilities, Discord-focused instruments, and a malware builder.
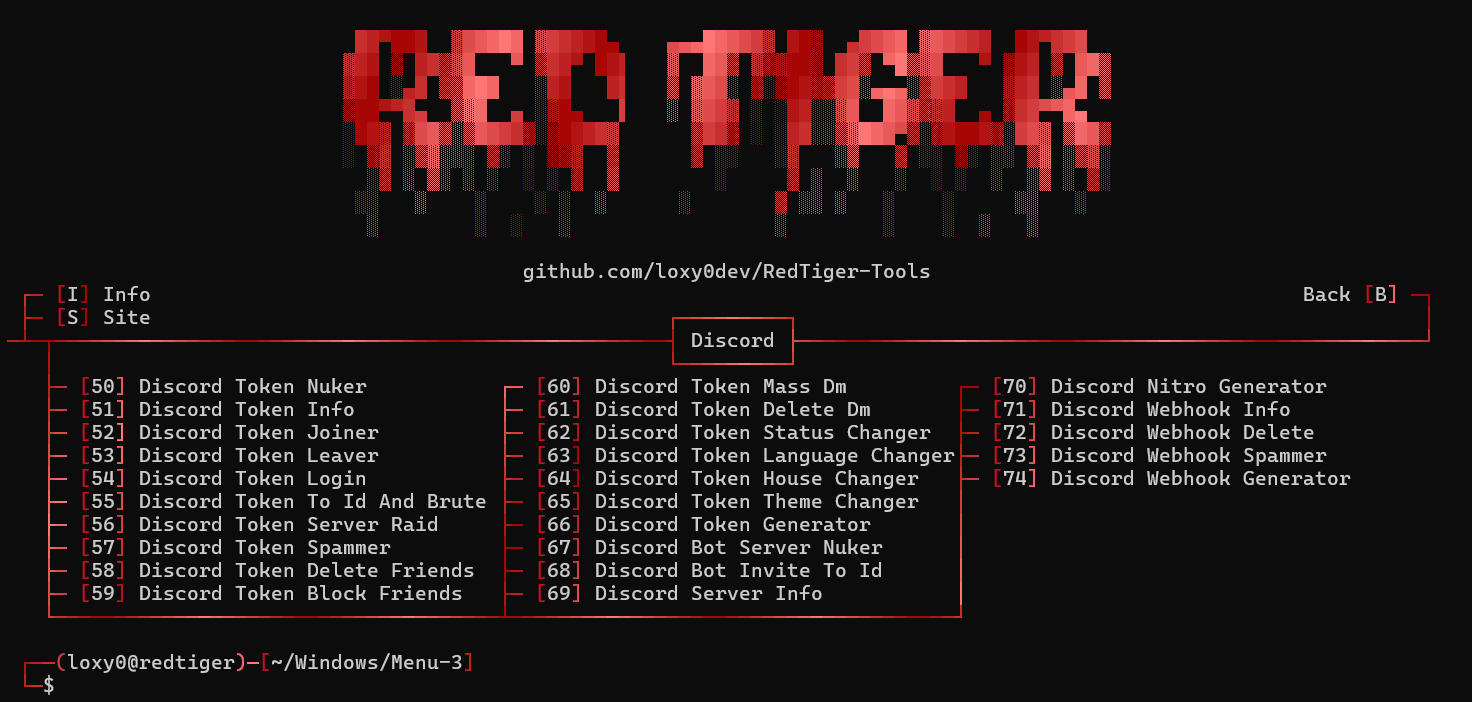
Supply: GitHub
RedTiger’s info-stealer part affords the usual capabilities of snatching system data, browser cookies and passwords, crypto pockets recordsdata, recreation recordsdata, and Roblox and Discord information. It may possibly additionally seize webcam snapshots and screenshots of the sufferer’s display.
Though the challenge marks its harmful features as “authorized use solely” on GitHub, its free and unconditional distribution and the shortage of any safeguards permit simple abuse.
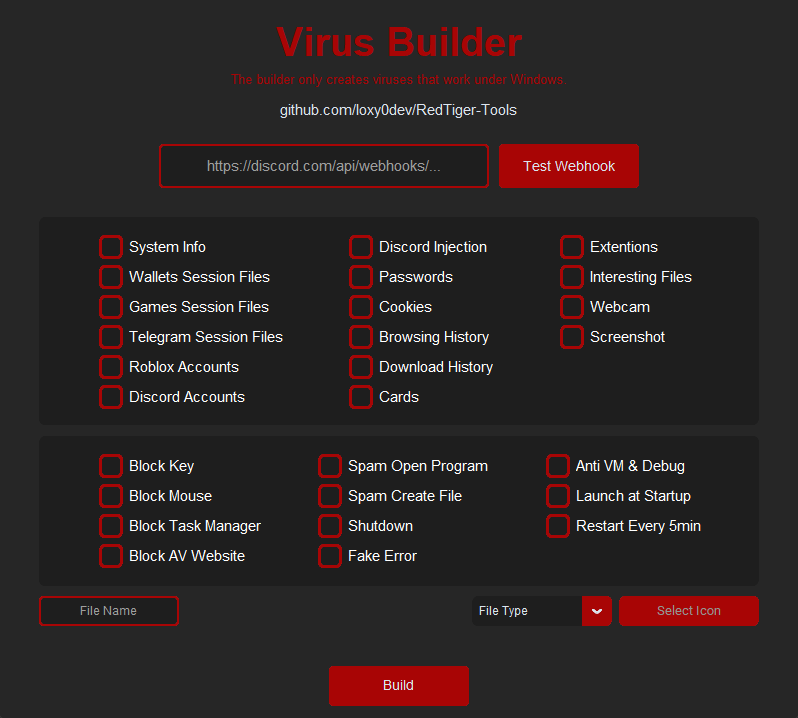
Supply: GitHub
In keeping with a report from Netskope, menace actors at the moment are abusing RedTiger’s info-stealer part, primarily for focusing on French Discord account holders.
The attackers compiled RedTiger’s code utilizing PyInstaller to type standalone binaries and gave these gaming or Discord-related names.
As soon as the info-stealer is put in on the sufferer’s machine, it scans for Discord and browser database recordsdata. It then extracts plain and encrypted tokens through regex, validates the tokens, and pulls the profile, e-mail, multi-factor authentication, and subscription info.
Subsequent, it injects customized JavaScript into Discord’s index.js to intercept API calls and seize occasions similar to login makes an attempt, purchases, and even password adjustments. It additionally extracts cost info (PayPal, bank cards) saved on Discord.
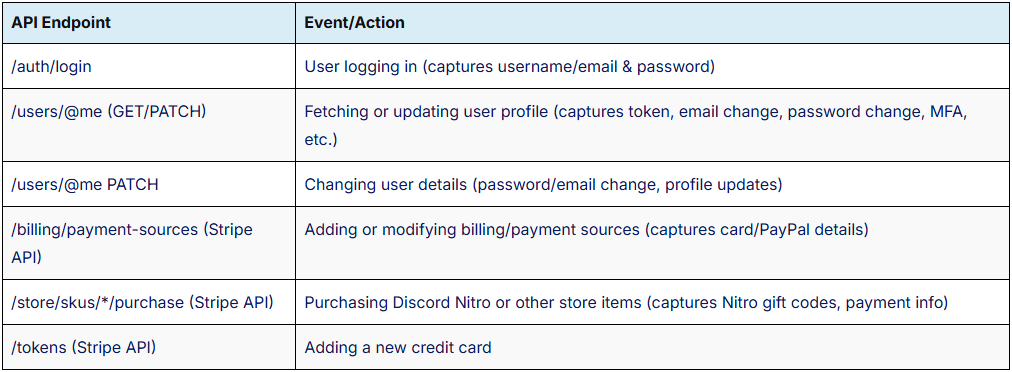
Supply: Netskope
From the sufferer’s net browsers, RedTiger harvests saved passwords, cookies, historical past, bank cards, and browser extensions. The malware additionally captures desktop screenshots and scans for .TXT, .SQL, and .ZIP recordsdata on the filesystem.
After amassing the info, the malware archives the recordsdata and uploads them to GoFile, a cloud storage service that permits nameless uploads. The obtain hyperlink is then despatched to the attacker through a Discord webhook, together with the sufferer metadata.
Relating to evasion, RedTiger is well-equipped, that includes anti-sandbox mechanisms and terminating when debuggers are detected. The malware additionally spawns 400 processes and creates 100 random recordsdata to overload forensic evaluation.
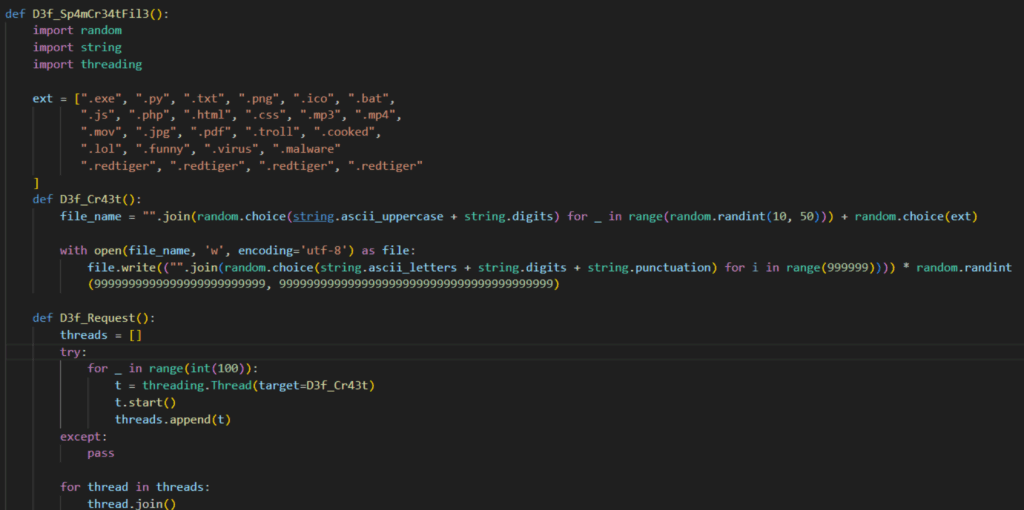
Supply: Netskope
Whereas Netskope has not shared specific distribution vectors for the weaponized RedTiger binaries, some widespread strategies embrace Discord channels, malicious software program obtain websites, discussion board posts, malvertising, and YouTube movies.
Customers ought to keep away from downloading executables or recreation instruments like mods, “trainers,” or “boosters” from unverified sources.
If you happen to suspect compromise, revoke Discord tokens, change passwords, and reinstall your Discord desktop shopper from the official web site. Additionally, clear saved information from browsers and allow MFA in all places.


