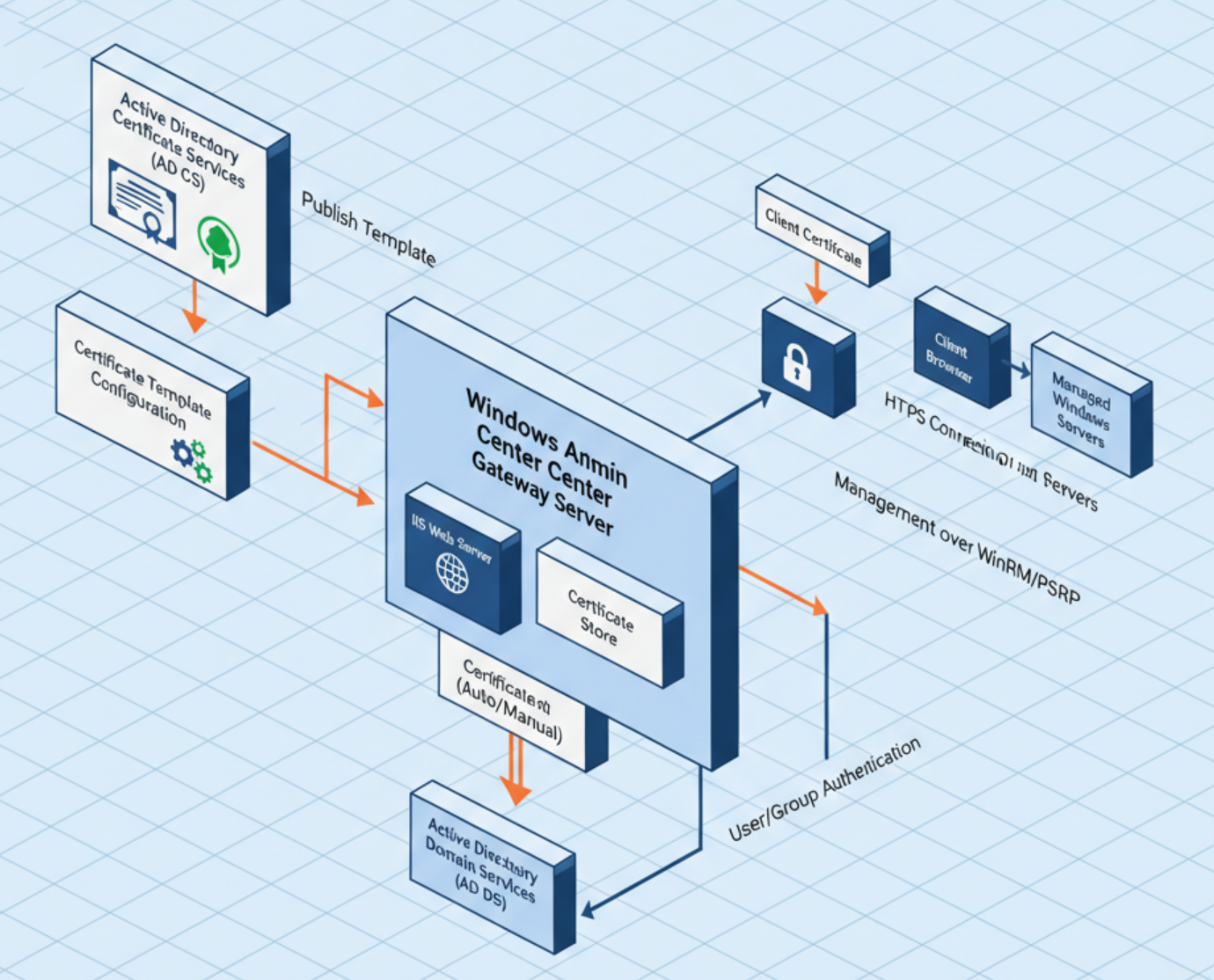
Implementing certificate-based authentication for Home windows Admin Middle (WAC) entails leveraging sensible card login (person certificates) in Energetic Listing. In a manufacturing Energetic Listing surroundings, you possibly can require directors to authenticate with a shopper certificates. These are sometimes saved on a sensible card or digital sensible card, earlier than the administrator they will entry the WAC gateway. That is achieved through the use of Energetic Listing Certificates Providers (AD CS) to concern logon certificates to customers and configuring Authentication Mechanism Assurance (AMA) in Energetic Listing to tie these certificates to a safety group. WAC is then configured to permit entry solely to customers who current the authorised certificates (by way of membership within the particular group). The result’s that solely customers who’ve authenticated with a sound sensible card certificates can entry WAC, including a robust second issue past passwords.
Earlier than configuring certificate-based auth for WAC, guarantee the next stipulations are in place:
- Energetic Listing Area: WAC and customers should reside in an AD area.
- AD CS (PKI) Deployment: An enterprise Energetic Listing Certificates Providers Certification Authority must be put in and trusted by the area.
- Sensible Card Infrastructure: Customers will want sensible card gadgets or digital sensible playing cards. This may very well be a bodily sensible card + reader for every admin, or a TPM-backed digital sensible card (VSC) on their machine. Every person should have a private certificates that will probably be used for logon.
- Home windows Admin Middle: WAC must be put in in gateway mode on a domain-joined Home windows Server. For manufacturing, exchange the default self-signed certificates WAC generates with an SSL certificates issued by your CA that matches the WAC gateway’s DNS identify.
- WAC Gateway Entry Teams: Resolve which AD safety group(s) will probably be allowed as gateway customers in WAC. Additionally create or establish a gaggle to make use of for the smartcard enforcement. For instance, create a gaggle referred to as “WAC-CertAuth-Required” (World/Common scope). No members will probably be straight added to this group. Membership will probably be assigned dynamically by way of AMA primarily based on logon methodology.
- Area Controller Certificates: Guarantee your area controllers have legitimate certificates for Kerberos PKINIT (Area Controller Authentication certificates). Enterprise CAs normally auto-enroll these. This ensures DCs can settle for sensible card logons. Additionally confirm DCs can attain the CRL distribution factors in your CA certificates to test revocation.
- Group Coverage for Sensible Playing cards: It’s beneficial to implement sure insurance policies: e.g., allow “Interactive logon: Require sensible card” on accounts or techniques if you wish to forestall password logon solely for these accounts, and allow “Sensible card elimination conduct: Lock workstation” on shopper PCs to auto-lock when a sensible card is eliminated. Additionally think about enabling “All the time await the community at laptop startup and logon” to keep away from cached logons interfering with AMA group project.
First, arrange a certificates template in AD CS in your directors’ logon certificates. You may both use the built-in Smartcard Logon template or create a devoted one:
- Create a Devoted Template: In your CA, open the Certificates Templates console. Duplicate the Smartcard Logon template (or the Person template with changes) so you possibly can customise it. Give it a reputation like “IT Admin Smartcard Logon”. Within the template’s properties, configure the next key settings:
- Compatibility: Guarantee it’s set for no less than Home windows Server 2008 R2 / Home windows 7 for full sensible card help.
- Cryptography: Select a robust key size (2048 or larger) and CSP/KSP supporting your sensible playing cards. Allow “Immediate for PIN on use” if obtainable.
- Topic Identify: Set to “Construct from this AD data” utilizing the person’s Person principal identify (UPN). The UPN will probably be included within the certificates’s topic different identify. That is crucial because the area controller makes use of the certificates’s UPN to map to the person account throughout logon.
- Extensions: Underneath Software Insurance policies (Prolonged Key Utilization), guarantee Sensible Card Logon (OID 1.3.6.1.4.1.311.20.2.2) is current. You might also embody Consumer Authentication (1.3.6.1.5.5.7.3.2) if customers may authenticate to different companies. Take away any EKUs not wanted. Additionally, guarantee “Signature and Smartcard Logon” or comparable is chosen because the issuance coverage if related.
- Safety: Assign Enroll (and Learn) permissions to the person group that may obtain these certificates (e.g. your IT admins group), and to the enrollment brokers if utilizing one.
- Expiration: Set an applicable validity interval (e.g. 1 or 2 years) and publish well timed CRLs so expired/revoked certs are acknowledged.
This course of will generate a singular Object Identifier (OID) for the brand new template (seen on the Normal tab or by way of certutil -template). Pay attention to this template OID, as we’ll use it for AMA mapping. (If utilizing the built-in Smartcard Logon template, it has a default OID you possibly can acquire equally.)
- Publish the Template: In case you created a brand new template, publish it on the CA (so it’s obtainable for enrollment). Within the Certificates Authority MMC, right-click Certificates Templates > New > Certificates Template to Problem, and choose your template.
- Enroll Certificates to Admins: Enroll every administrator for a sensible card certificates utilizing this template. Sometimes, that is finished through the use of the Certificates MMC on a shopper with a sensible card reader:
o Have the person insert their sensible card and open certmgr.msc (or use a devoted sensible card enrollment instrument if obtainable).
o Enroll for the “IT Admin Smartcard Logon” certificates. This can generate a non-public key on the cardboard and concern the certificates to the cardboard. The certificates ought to now reside within the person’s Private retailer and on the cardboard.
o Make sure the certificates reveals the proper UPN within the Topic Various Identify and the Sensible Card Logon coverage within the Software Insurance policies.
- Confirm AD Belief of the Certificates: As a result of that is an enterprise CA, the issued certificates will robotically be trusted by Energetic Listing for logon (the CA’s root is within the NTAuth retailer). Simply to be protected, verify that the CA’s root cert is current within the NTAuthCertificates container in AD (use certutil -viewstore -enterprise NTAuth). If not, publish it utilizing certutil -dspublish -f rootcert.cer NTAuth. This ensures area controllers belief certificates from this CA for authentication.
At this stage, every admin person ought to have a sound sensible card logon certificates issued by AD CS, which incorporates an OID figuring out the template. Subsequent, we’ll configure Energetic Listing to acknowledge this OID and hyperlink it to a safety group by way of Authentication Mechanism Assurance.
Authentication Mechanism Assurance (AMA) is an Energetic Listing function that provides a person to a safety group dynamically after they go online with a certificates that comprises a particular issuer coverage or template OID. We are going to use AMA to flag customers who authenticated with our sensible card certificates. The plan is to map the OID of our “IT Admin Smartcard Logon” certificates template to a particular safety group (e.g. “WAC-CertAuth-Required”). When a person logs on with that certificates, area controllers will robotically embody this group within the person’s Kerberos token; in the event that they go online with a password or different methodology, they received’t have this group.
Comply with these steps to configure AMA:
- Create a Common Safety Group: If not already created, make a brand new safety group in AD (ideally within the Customers container or a devoted OU) named for instance “WAC-CertAuth-Required”. Make it a common group (beneficial for AMA) and set scope to Safety. Don’t add any members to it as AMA will management membership. Additionally, don’t use this group for every other assignments besides this objective.
- Discover the Certificates Template OID: Find the OID of the certificates template you might be utilizing:
o Open the properties of the certificates template within the Certificates Templates console. On the Normal tab notice the Template OID (e.g. 1.3.6.1.4.1.311.x.x.xxxxx.xxxx…). Alternatively, use Get-CATemplate
o In case you used the built-in Smartcard Logon template, its OID could be discovered equally (every template has a singular OID).
- Map the OID to the Group in AD: This step requires modifying the AD Configuration partition utilizing ADSI Edit or PowerShell:
o Open ADSI Edit (adsiedit.msc) as an enterprise admin.
o Proper-click ADSI Edit > Connect with…. Choose Configuration well-known naming context.
o Navigate to CN=Public Key Providers,CN=Providers,CN=Configuration,
o Search for an object whose msPKI-Cert-Template-OID attribute matches the OID of your certificates template. The objects are sometimes named after the template or have a GUID. You could want to examine every till you discover the matching OID worth.
o As soon as discovered, open the properties of that OID object. There will probably be an attribute msDS-OIDToGroupLink. That is the place we hyperlink the OID to a gaggle.
o Copy the distinguishedName of the “WAC-CertAuth-Required” group you created (yow will discover it by connecting ADSI Edit to the Default naming context, finding the group, and copying the DN).
o Within the OID object’s properties, set msDS-OIDToGroupLink to the DN of your group. Apply the change.
This mapping tells AD: for any person logging in with a certificates issued from this template OID, embody the required group of their token.
A fast method to verify the mapping is working is to strive including a member to the “WAC-CertAuth-Required” group in AD Customers & Computer systems. It ought to forestall you from manually including any members now, giving an error like “OID mapped teams can’t have members.”. That is anticipated because the group is now managed by AMA.
Now AMA is configured. When a person authenticates with our sensible card cert, the area controller will consider the certificates, see the template OID, and if it matches the mapped OID, will add the “WAC-CertAuth-Required” group SID to the person’s Kerberos token. If the person logs on with username/password, that group will not be current.
AMA triggers solely throughout interactive logon (or unlock) when the person truly makes use of the certificates to go online to Home windows. It does not dynamically add/take away teams in the midst of a session. This implies the person should log onto their machine with the sensible card certificates to get the group.
WAC helps two id suppliers for gateway entry: Energetic Listing (default) or Microsoft Entra ID. We’re utilizing AD with an added sensible card requirement. WAC gives a setting to require membership in a “smartcard authentication group” along with the traditional person group.
Do the next on the WAC gateway server (whereas logged in as a WAC gateway administrator or native admin):
- Open WAC Entry Settings: In an internet browser, entry the Home windows Admin Middle portal (e.g. https://
). Go to the Settings (gear icon) > Entry panel. Guarantee “Use Energetic Listing” (or “Use Home windows Entry Management”) is chosen because the id supplier, since we’re utilizing AD teams. - Configure Gateway Customers Group(s): Underneath Person Entry, it is best to see an choice to specify who can entry the WAC gateway (“Gateway customers”). By default, if no group is listed, any authenticated person can entry. Add your directors group (or teams) right here to limit WAC entry to solely these customers. For instance, add “IT Admins” or no matter AD group comprises the admins that ought to use WAC. After including, it would present up within the record of allowed person teams.
- Allow Smartcard Enforcement: Nonetheless within the Entry settings, search for the Smartcard authentication possibility if you add . WAC permits specifying an extra required group that signifies sensible card utilization. Add the “WAC-CertAuth-Required” (the AMA-linked group) right here because the Smartcard-required group. Within the WAC UI, this is perhaps finished by clicking “+ Add smartcard group” or marking one of many added teams as a smartcard group. (In some variations, you first add the group beneath Customers, then test a field to designate it as a smartcard-enforced group.)
o After this configuration, WAC’s efficient entry test turns into: a person’s AD account should be a member of no less than one allowed group and should be a member of the required smartcard group. This corresponds precisely to requiring certificates logon. In line with Microsoft’s documentation: “After getting added a smartcard-based safety group, a person can solely entry the WAC service if they’re a member of any safety group AND a smartcard group included within the customers record.”. In our case, meaning the person should be in (for instance) “IT Admins” and in “WAC-CertAuth-Required”. The latter solely occurs after they’ve logged on with the certificates, so successfully the person should be utilizing their sensible card.
- Configure Gateway Directors (if wanted): If there are others who will administer the WAC gateway settings, you can too add teams/customers beneath the Directors tab. You can even implement a smartcard group on directors equally. Sometimes, native Directors on the server have already got admin entry to WAC by default. Be certain these accounts additionally use sensible playing cards otherwise you exclude accounts accordingly for safety.
- Save Settings: Save or apply the Entry settings. The WAC gateway service could restart to use adjustments.
You may confirm WAC entry settings by way of PowerShell on the WAC server. Open PowerShell and use: Get-SMEAuthorization (if obtainable) or test the configuration file. WAC shops allowed teams and the smartcard-required group. Make sure the output lists your teams appropriately. There’s additionally a PowerShell (Set-SMEAuthorization) to configure these settings in the event you choose scripting (documentation covers utilizing -RequiredGroups and -RequiredSmartCardGroups parameters for WAC).
At this level, WAC is configured to require certificate-based authentication. The gateway will carry out Home windows Built-in Authentication (Kerberos/NTLM) as standard, however it would solely authorize the session if the person’s token comprises the smartcard group SID along with an allowed group SID. If the person logged in with a password, the smartcard group SID is lacking and WAC will deny entry (HTTP 401/403).
It’s essential to check the setup end-to-end to find out if the configuration capabilities as anticipated.:
- Take a look at Case 1. Password login (must be denied): Have an admin person try and entry WAC with out utilizing their sensible card. For instance, the person can signal out and go online to Home windows with simply username/password (or disable their sensible card login quickly). Then navigate to the WAC URL. The WAC web site will immediate for authentication (the browser will strive Built-in Home windows Auth). The person could also be prompted to authenticate; if that’s the case, even getting into appropriate AD credentials ought to end in entry denied on the gateway. The person will see a 401 Unauthorized error from WAC after login, or WAC will hold prompting for credentials. That is anticipated as a result of though the person is within the allowed admin group, they don’t seem to be within the AMA smartcard group (since they logged on with a password). WAC will refuse entry because the AND situation shouldn’t be met. This confirms {that a} password-only login is inadequate.
- Take a look at Case 2. Sensible card login (must be allowed): Now have the person log out and go online to Home windows utilizing the sensible card. (On the Home windows login display screen, they need to insert the cardboard, select the sensible card login possibility, and enter the PIN. This makes use of their certificates to authenticate to AD.) After interactive logon with the sensible card, the person’s Kerberos ticket now consists of the “WAC-CertAuth-Required” group, courtesy of AMA. Now entry the WAC portal once more (e.g. by way of Microsoft Edge or Chrome). The browser will carry out Built-in Auth (which can use the logged-on person’s credentials/ticket). The person must be granted entry to WAC this time and see the same old WAC interface. No extra prompts happen. WAC sees the person is in each required teams and permits the connection.
- Verify Group Presence: On the person’s machine, you possibly can run whoami /teams in a command immediate after logging in with the sensible card. You must see the “WAC-CertAuth-Required” group listed within the teams. In case you log in with password, that group won’t be listed. This can be a fast method to confirm AMA is working as supposed.
- WAC Logging: Within the Home windows Admin Middle server, test the occasion log “Microsoft-ServerManagementExperience” (beneath Purposes and Providers Logs) for any related warnings or errors. When a person is denied as a result of not assembly group necessities, WAC will usually log an occasion indicating the person’s id was not approved. This may help verify that the smartcard requirement was the rationale (versus different failures).
- Edge/Browser Conduct: If the browser pops up a Home windows Safety login dialog repeatedly even after utilizing the sensible card, ensure the location is in Intranet Zone or Trusted Websites in order that Built-in Auth is seamless. Additionally make sure the person’s certificates authentication to the area is functioning (they’ve a Kerberos TGT). Normally, after a sensible card desktop login, the browser shouldn’t immediate in any respect. It ought to silently use the prevailing Kerberos ticket.
By finishing these checks, you validate that the system is appropriately distinguishing certificate-based logons from password logons when gating WAC entry.
Regardless of cautious setup, you may encounter points. Listed here are widespread issues and their options:
- Person not being added to AMA Group: After logging on with a sensible card, if whoami /teams doesn’t present the “WAC-CertAuth-Required” group:
o Confirm the certificates was issued from the proper template (test the certificates’s particulars: beneath Particulars, Certificates Template Data ought to present your template identify/OID).
o Confirm the OID mapping in ADSI Edit is appropriate (no typos within the DN, and it’s in the proper OID object).
o The group should be common scope if in a multi-domain forest. If it’s world and the person/DC are in one other area, it may not be assigned. Use Common as beneficial.
o Guarantee area purposeful stage is 2008 R2 or larger; AMA received’t work under that.
o If the person is logging on to a machine that’s offline (no DC contact) and utilizing cached credentials, AMA received’t apply because the DC can’t consider the certificates. The “All the time await community at logon” GPO setting (Pc Configuration → System → Logon) must be enabled to power on-line logon. If the person should logon cached (like laptop computer off VPN), they received’t get the AMA group till they will contact a DC (which might then occur after they entry area assets).
o Test the Occasion Go surfing the Area Controller dealing with the logon (Safety log). Search for occasion 4768 or 4771 across the logon time:
-
-
- 4771 with Failure Code 0x12 or textual content about “Encryption sort not supported” may point out a lacking DC certificates or Kerberos settings concern.
- Errors about “The certification authority shouldn’t be trusted” or “Smartcard logon shouldn’t be supported for person” point out belief issues. Be certain the CA cert is in NTAuth and the person cert has the correct UPN.
- In case you see Occasion 19 within the System go online the DC (KDC occasion for failed sensible card logon), it usually offers a purpose code. For instance, “KDC certificates lacking” or “No legitimate CRL” and so forth.
-
o One fast test: run on a DC certutil -verify -urlfetch
o If the person’s certificates doesn’t have the Sensible Card Logon EKU and also you as a substitute tried utilizing simply Consumer Authentication: area controllers by default require the particular Smartcard EKU (or the brand new “Kerberos Authentication” EKU in newer domains). Be certain the template included the proper EKU for sensible card logon, in any other case the DC could not deal with it as a sensible card login try in any respect.
- Person can log in to WAC with password (not anticipated): If by some means a person was capable of entry WAC with out utilizing the sensible card:
o Double-check WAC’s Entry settings. Maybe the smartcard-required group wasn’t correctly added. On the WAC server, run Get-SMEAcls or test the config to make sure the RequiredSmartcardGroups attribute consists of the proper group SID.
o Verify the person’s account isn’t in that smartcard group completely (nobody must be a direct member; AMA teams should not have any static members). Use ADUC or PowerShell to make sure the group has no members attribute set. If somebody manually added a person to that group, then that person will bypass the necessity for a cert (they at all times have the group). Take away any unintended members. “OID mapped teams can’t have members” enforcement ought to forestall this, but when the mapping was flawed and never truly utilized, somebody may need populated the group. Repair the mapping and clear members.
o Make sure the person didn’t by some means have the AMA group from a earlier sensible card logon cached. A identified caveat: If a person beforehand logged on with a sensible card after which logs off and again on with a password on the identical machine and not using a reboot, Home windows may cache the group within the token (as a result of an optimization). This could occur with “quick logon” or unlock situations. The repair is the GPO talked about (disable quick logon). In follow, a recent reboot + password logon ought to drop the group. Warn customers that switching from smartcard to password login on a machine with out reboot may very well be inconsistent. It’s most secure to at all times use the sensible card, or reboot if they have to log in with password for some purpose.
o If utilizing distant desktop to WAC server or a bounce field, guarantee the identical certificates enforcement is taken into account there. If somebody logs into the bounce field with a password after which tries to make use of WAC, they’ll fail. That’s anticipated. They need to RDP with sensible card as nicely (RDP helps sensible card logon pass-through).
- Repeated credential prompts when accessing WAC: If a person who logged in with a sensible card nonetheless will get prompted for credentials within the browser:
o Make sure the browser is configured for built-in authentication. For Web Explorer/Edge (IE mode), the WAC URL must be within the Native Intranet zone (which normally permits computerized Home windows auth). For contemporary Edge/Chrome, they sometimes robotically try desktop credentials, but when not, you possibly can go to edge://settings -> Automated profile switching or edge://flags for built-in auth, or use group coverage “Built-in Home windows Authentication” to permit the WAC URL. In Chrome, you possibly can run it with –auth-server-whitelist=”wacservername.area.com”.
o If the browser prompts for a certificates choice (some configuration may trigger the location to request shopper cert at TLS stage), that’s not default for WAC. WAC by itself doesn’t use TLS client-cert authentication, so that you shouldn’t see a certificates choice popup. In case you do, maybe you or somebody configured the HTTP.sys binding on the WAC server to Require Consumer Certificates. That’s not needed for this answer (and would intervene, as WAC isn’t anticipating to parse shopper certs itself). If enabled, think about disabling that requirement, as our strategy makes use of Kerberos group membership as a substitute. Take away any guide netsh http shopper cert negotiation settings until you have got a particular purpose.
o Test that the person’s sensible card credential was cached in Home windows correctly. Typically after a recent logon, the primary hit to a safe web site may set off a PIN immediate if the browser tries to make use of the certificates for TLS or one thing. Make sure the PIN was entered throughout login and remains to be legitimate (some sensible playing cards may require PIN re-entry for signing, however normally not for Kerberos since Kerberos is already obtained at logon).
o Lastly, verify that the person’s Home windows session certainly has the AMA group. If not, WAC will hold prompting as a result of it sees the person in allowed group however not in smartcard group, and may deal with them as unauthorized (inflicting the browser to immediate once more). This can end in a 401. You may see the immediate come up repeatedly after which a clean web page. In WAC’s log, an occasion or error saying the person shouldn’t be approved will verify it. The answer is to get the AMA group within the token (log in with the cardboard correctly, repair AMA if damaged).
- Sensible card login fails on Home windows: That is extra of a PKI/AD concern than WAC concern:
o If when inserting card at logon, you get messages like “The system couldn’t log you on” or “No legitimate logon servers” or “certificates not acknowledged,” debug the sensible card logon itself. Frequent causes: the person certificates is lacking the UPN or has a UPN that doesn’t match the account, the CA that issued it isn’t in NTAuth or not trusted by the shopper or DC, or the DC’s personal certificates is lacking (test DC has a cert in its private retailer issued by your CA for area controller authentication).
o On the shopper, when the logon fails, you possibly can typically hit “Change Person -> Sensible card logon” and see if it lists the certificates. If not, the cardboard middleware may not be put in or working. If it lists it however errors after PIN, then seemingly an AD belief concern. Area controller safety log could have particulars.
- Certificates Revocation points: If a person’s certificates was revoked or expired, clearly they received’t be capable of authenticate with it. The DC will deny the sensible card logon (occasion will point out revoked or expired cert). The person would fall again to password (if allowed) which then received’t grant WAC entry. The repair is to resume their certificates prematurely. All the time hold observe of expiry dates and set reminders.
- Updating Certificates: When an admin will get issued a brand new sensible card or cert (or their cert is renewed with a brand new OID template), guarantee your AMA mapping covers it. In case you created a brand new template (with a brand new OID) for any purpose, you need to map that OID as nicely. AMA can map a number of OIDs by linking them to probably totally different teams. WAC solely helps one smartcard group in settings, so ideally you’d hold utilizing the identical template OID for all admin certs. If a brand new OID is required (say you have got a number of CAs or totally different templates), you could possibly map it to the identical group or embody a number of teams in WAC (although the UI helps one, you may workaround by nesting teams or including a number of allowed combos). Less complicated is to stay to 1 cert template for this objective.
- Group Coverage caching: The AMA group inclusion occurs on the Kerberos TGT stage. If a person logs on with sensible card, will get the group, then later the group mapping is eliminated or modified, an present TGT may nonetheless have the group till it expires (~10 hours by default). Clearing the Kerberos ticket (by klist purge or logoff) would take away it. Hold this in thoughts throughout adjustments: in the event you take away the mapping or change group, there may very well be a latency till all tickets expire or customers logoff.
- Alternate entry strategies: If somebody tries to make use of PowerShell Remoting (Enter-PSSession) or different instruments to hook up with the WAC gateway, they’ll nonetheless endure the identical test. Sometimes WAC is accessed by way of internet, however simply know the Home windows auth is at play no matter interface.
When utilizing certificate-based authentication for WAC by way of this methodology, pay attention to the next limitations or issues:
- Area-Joined Purchasers Required: This answer assumes admins are utilizing domain-joined Home windows machines for WAC entry (in order that their sensible card logon yields a Kerberos token with the group). If an admin tries to entry WAC from a non-domain system (the place they will’t do a Home windows built-in logon), they’d be prompted for credentials. They may technically insert their sensible card and choose it within the browser when prompted for credentials, however that will try a certificates mapping at WAC which isn’t configured. WAC does not natively help direct shopper certificates mapping on the internet software layer. The one supported method is by way of AD group as we’ve finished. So in follow, non-domain or exterior entry must be finished by way of a safe methodology (e.g. VPN into area or utilizing Azure AD integration as talked about). That is by design as WAC depends on Home windows Authentication, not varieties or client-cert internet auth.
- No Native OTP/MFA Immediate: In contrast to some internet apps, WAC itself doesn’t have a secondary immediate for OTP or comparable. The sensible card enforcement leverages the Home windows login. So there’s no separate UI in WAC for “insert your certificates”. It’s all clear as soon as arrange. As such, you possibly can’t combine password + cert in a single login to WAC because it’s one or the opposite by way of how the person logged into Home windows.
- Single Smartcard Group Restrict: WAC’s configuration permits just one “smartcard-required” group to be set. In case you had totally different ranges of assurance or a number of certificates profiles, you may have to create a standard group that each one certificate-authenticated customers get. For instance, in the event you concern totally different certs (say some with larger assurance), you might map a number of OIDs to the identical AMA group in order that any of them will fulfill the WAC test. Plan your AMA mappings accordingly (you possibly can map a number of OIDs to 1 group by concatenating DNs within the msDS-OIDToGroupLink, or by having a number of template OID objects level to the identical group DN).
- Auditing: Observe that when customers entry WAC with this setup, the logon audit on the WAC server will present a standard Kerberos login by the person. There isn’t an express occasion on the WAC server saying “used certificates”. The proof of certificates use is within the DC’s logs (Kerberos AS ticket was obtained by way of sensible card). So, auditing clever, you may correlate that if a person accessed WAC and had the AMA group, it means they used a sensible card. If auditing that’s essential, guarantee to retain area safety logs. You would additionally arrange a scheduled process and script to log an occasion on the WAC server when a person missing the group tries to attach (e.g., monitor WAC error occasions for unauthorized entry).