Germany’s home intelligence company is warning of suspected state-sponsored menace actors concentrating on high-ranking people in phishing assaults by way of messaging apps like Sign.
The assaults mix social engineering with respectable options to steal knowledge from politicians, navy officers, diplomats, and investigative journalists in Germany and throughout Europe.
The safety advisory is primarily based on intelligence collected by the Federal Workplace for the Safety of the Structure (BfV) and the Federal Workplace for Info Safety (BSI).
“A defining attribute of this assault marketing campaign is that no malware is used, nor are technical vulnerabilities within the messaging companies exploited,” the 2 businesses inform.
In accordance with the advisory, the attackers contact the goal instantly, pretending to be from the assist crew of the messaging service or the assist chatbot.
“The objective is to covertly achieve entry to one-to-one and group chats in addition to contact lists of the affected people,”
There are two variations of those assaults: one which performs a full account takeover, and one which pairs the account with the attacker’s machine to watch chat exercise.
Within the first variant, the attackers impersonate Sign’s assist service and ship a faux safety warning to create a way of urgency.
The goal is then tricked into sharing their Sign PIN or an SMS verification code, which permits the attackers to register the account to a tool they management. Then they hijack the account and lock out the sufferer.
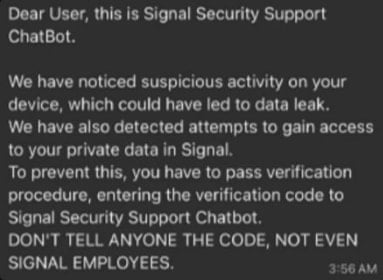
Supply: BSI
Within the second case, the attacker makes use of a believable ruse to persuade the goal to scan a QR code. This abuses Sign’s respectable linked-device characteristic that permits including the account to a number of gadgets (laptop, pill, telephone).
The result’s that the sufferer account is paired with a tool managed by the unhealthy actor, who will get entry chats and contacts with out elevating any flags.
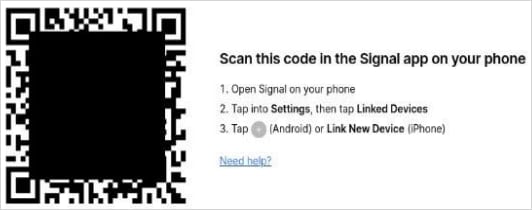
Supply: BSI
Though Sign lists all gadgets hooked up to the account beneath Settings > Linked gadgets, customers not often examine it.
Such assaults have been noticed to happen on Sign, however the bulletin warns that WhatsApp additionally helps related performance and will be abused in the identical means.
Final 12 months, Google menace researchers reported that the QR code pairing approach was employed by Russian state-aligned menace teams similar to Sandworm.
Ukraine’s Laptop Emergency Response Crew (CERT-UA) additionally attributed related assaults to Russian hackers, concentrating on WhatsApp accounts.
Nevertheless, a number of menace actors, together with cybercriminals, have since adopted the approach in campaigns like GhostPairing to hijack accounts for scams and fraud.
The German authorities counsel that customers keep away from replying to Sign messages from alleged assist accounts, because the messaging platform by no means contacts customers instantly.
As a substitute, recipients of those messages are really helpful to dam and report these accounts.
As an additional safety step, Sign customers can allow the ‘Registration Lock’ choice beneath Settings > Account. As soon as energetic, Sign will ask for a PIN you set every time somebody tries to register your telephone quantity with the appliance.
With out the PIN code, the Sign account registration on one other machine fails. Because the code is important for registration, shedding it may end up in shedding entry to the account.
It is usually strongly really helpful that customers repeatedly assessment the checklist of gadgets with entry to your Sign account beneath Settings → Linked gadgets, and take away unrecognized gadgets.
Fashionable IT infrastructure strikes quicker than handbook workflows can deal with.
On this new Tines information, find out how your crew can scale back hidden handbook delays, enhance reliability by means of automated response, and construct and scale clever workflows on high of instruments you already use.



