Cloud market and distributor Pax8 has confirmed that it mistakenly despatched an e-mail to fewer than 40 UK-based companions containing a spreadsheet with inner enterprise data, together with MSP buyer and Microsoft licensing knowledge.
Pax8 is a fast-growing cloud commerce market with greater than 1,700 staff, over 47,000 companions worldwide, and operations in 18 nations. The corporate lately surpassed $2 billion in annual income, with notably sturdy development in Europe.
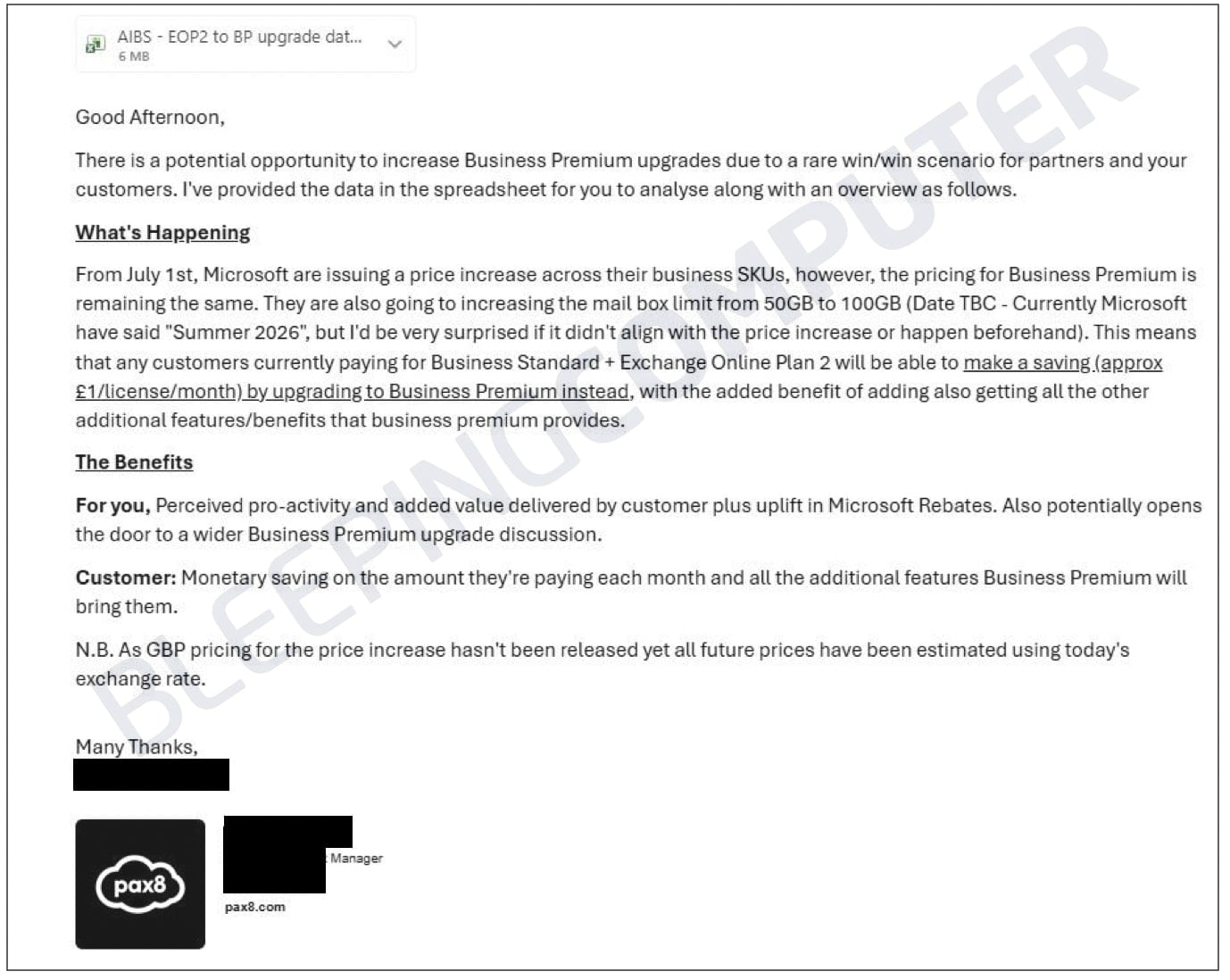
CSV exposes buyer and licensing knowledge
The e-mail, titled “Potential Enterprise Premium Improve Tactic to Save Cash,” was despatched on January 13 by an EMEA-based strategic account supervisor and included a CSV attachment.
In line with Pax8, the file contained inner pricing and Microsoft program data affecting roughly 1,800 companions, primarily within the UK, with one in Canada—and was by chance distributed to fewer than 40 UK-based recipients.
MSPs who obtained the message informed BleepingComputer that the CSV file listed buyer group names, Microsoft SKUs, license counts, and New Commerce Expertise (NCE) renewal dates.
Artifacts shared with BleepingComputer instantly by a number of recipients reveal that the leaked spreadsheet contained greater than 56,000 entries with fields equivalent to:
- Accomplice Identify and ID
- Buyer Identify and ID
- Vendor Identify and Product Identify
- Gross & Web Bookings
- Forex Complete Amount
- Territory
- Account Proprietor
- Provision Date
- Cancelled E book Date
- Postal Code
- Transaction Sort
- Dedication Time period Finish Date
Shortly after the e-mail was despatched, the sender tried to recall the message and later adopted up with one other e-mail asking recipients to delete the unique message and attachment, acknowledging it had been despatched in error:

Within the follow-up discover, Pax8 informed companions that the file didn’t comprise personally identifiable data however restricted enterprise data that might reveal MSP pricing and Microsoft program administration particulars. Such data, together with buyer portfolios and licensing footprints, would usually be seen solely to the MSP managing these tenants and Pax8 itself.
A number of recipients shared the wording from Pax8’s comply with up with BleepingComputer:
“Pricey Accomplice,
Earlier at present, 13 January 2026, a Pax8 worker mistakenly despatched an e-mail with an hooked up spreadsheet to fewer than 40 UK-based companions. The attachment didn’t comprise personally identifiable data. Nevertheless, the file included restricted inner enterprise data reflective of your Pax8 pricing and a few Microsoft program administration.
Importantly, there isn’t a impression to Market availability or safety controls on account of this incident.
What we did instantly
* Contacted every recipient instantly and requested deletion of the e-mail and attachment
* Required affirmation of deletion and non-forwarding
* Are conducting 1:1 follow-up calls with recipients to strengthen deletion and ensure completion
* Launched an inner overview to find out how this occurred and to stop recurrence
What you must do
No motion is required from you.
In case you have questions, please attain out to us at belief@pax8.com.
We acknowledge the accountability we’ve to guard partner-confidential data.
Sincerely,
Pax8 Alerts”
Menace actors reportedly searching for the dataset
BleepingComputer has additionally discovered from trade sources that menace actors are actually approaching some affected MSPs, providing to purchase copies of the uncovered dataset.
Such data could possibly be precious each to rivals and cybercriminals. For rival MSPs, the checklist might reveal which organizations use Pax8 as their distributor, the scale of every buyer’s Microsoft setting, contract renewal timelines, and probably the pricing tiers being paid—knowledge that could possibly be used for aggressive focusing on or poaching.
For menace actors, the dataset might operate as a high-quality focusing on checklist, figuring out organizations operating particular Microsoft merchandise, the dimensions of their deployments, and which MSP manages their setting. This might allow extra convincing phishing campaigns, enterprise e-mail compromise makes an attempt, or extortion efforts timed round license renewals and contract negotiations.
BleepingComputer approached Pax8’s media workforce for remark previous to publication, however messages to the listed press deal with repeatedly bounced. We additionally reached out to members of the communications workforce, the help desk, the belief@pax8.com inbox, and personnel acquainted with the incident.
A Pax8 spokesperson later confirmed the incident to BleepingComputer, aligning with particulars already disclosed within the firm’s public notices and accomplice communications.
It is price range season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the yr forward. This report compiles their insights, permitting readers to benchmark methods, establish rising traits, and examine their priorities as they head into 2026.
Find out how prime leaders are turning funding into measurable impression.



